Jobs in an AI-SOC
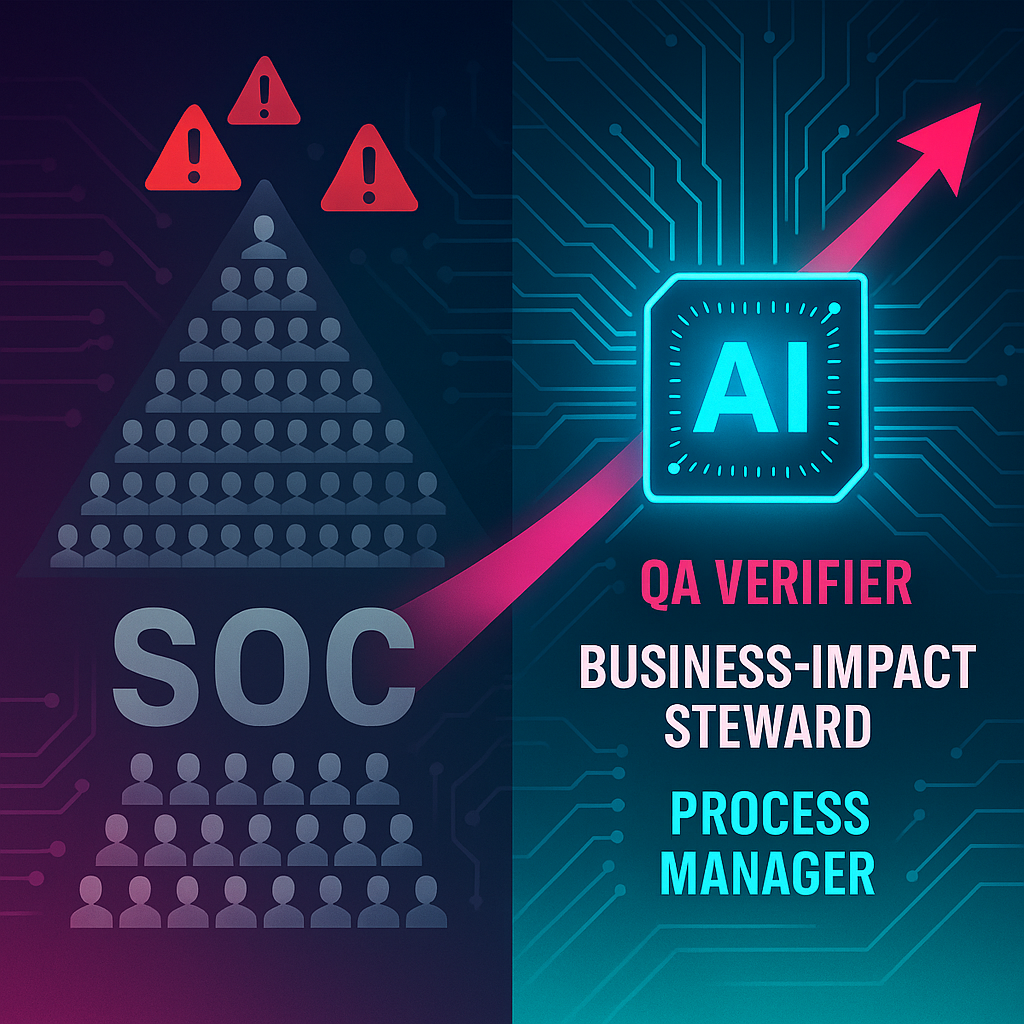
You feel the ground shifting—and you should. AI isn’t nibbling around the edges of the Security Operations Center (SOC); it’s coming straight for the jobs, the certifications, the conference booth swag, and the tool stacks that defined an analyst’s career. The hours you poured into SIEM query syntax, expensive SANS courses, and four-monitor war rooms suddenly look fragile. If an autonomous pipeline can triage, scope, and remediate in seconds, what’s left for you to engineer? The unease is rational: reputations, vendor ecosystems, and entire training industries stand to shrink. But fear alone won’t hold back the tide. Instead, we need to map how those same skills—re-channeled into quality assurance, process stewardship, and cost-efficient automation—will shape the next generation of SOC work. Let’s unpack that transition.
The Disappearance —and Evolution—of Entry-Level Triage
Triage has always been the SOC’s front line. Every alert, no matter how routine or rare, receives a first-pass verdict that determines whether an issue is ignored, escalated, or contained. That decision shapes everything downstream—from incident scope to executive briefings—so the work is critical. Yet the industry staffs it with entry-level people because the alert volume is too large, too relentless and too tedious, that it too costly and dull for senior personel.
AI changes the mechanics, not the importance, of this task. Automated pipelines can now enrich, correlate, and disposition alerts in real time, applying the collective experience of thousands of prior investigations with perfect consistency. Handing triage to software is therefore a quality upgrade, not a cost-cut: it removes timing pressures, fatigue, and the inevitable variance that comes from rotating six people through a 24 × 7 queue.
The analysts who once shouldered triage do not vanish; they move into quality-assurance review. Their new mission is to examine statistically selected AI decisions, confirm the logic, and flag edge cases the model missed. Think of it like learning guitar: no one begins by writing a song—they start by playing an existing piece, learning scales and progressions, and gradually understanding the structure. By auditing AI output, junior staff:
- Learn faster—they see complete investigations rather than isolated log entries.
- Protect accuracy—they catch misclassifications and feed them back to improve the model.
- Avoid burnout—they sample and verify instead of fighting an endless alert stream.
The head-count shrinks, but the role gains depth. Instead of being the last human checkpoint on the least informed decision, the former Tier-1 analyst becomes the first human safeguard on a machine-driven process—transforming triage from a volume game into an expertise accelerator.
The Shift in the Response Layer: From IOC Scoping to Business-Impact Stewardship
The mid-tier analyst’s job is about to shift. Up to now, their day has centered on the technical response—running database searches for file hashes or IP addresses, tracing every place a threat appears, and launching scripts to quarantine the affected machines. Those tasks are objective and repeatable, which makes them ideal for automation: modern pipelines can identify, trace, and isolate compromised assets in seconds, with fewer errors than a human scrolling through console pages.
What automation still can’t provide is the business response. Shutting down a payment gateway at noon on a Saturday or rebooting a hospital imaging server during clinic hours might neutralize malware, but it could also freeze revenue, violate a service-level agreement, or jeopardize patient care. The gap between what can be done technically and what should be done operationally demands human judgment—someone who understands how each system supports payroll runs, production deadlines, and customer commitments, and who can balance security risk against business impact in real time.
That judgment becomes the new center of gravity for mid-tier analysts. Instead of chasing indicators across logs, they maintain living maps that link servers and applications to cash-flow cycles, regulatory promises, and service guarantees. When an automated playbook proposes containment, they decide whether to execute it immediately, phase it after hours, reroute workflows through standby services, or defer action altogether. They then guide recovery so normal operations resume without data loss or contractual penalties. Their value now lies in aligning security actions with business priorities—protecting the organization without unintentionally stopping it from operating.
SOC Maturity becomes center Stage
The most sweeping change arrives at the top of the analyst ladder. The experts who once spent their days “threat hunting” across raw telemetry will spend far less time prowling the data and far more time managing the engine that hunts on their behalf. Their charter becomes process stewardship: ensuring that every detection rule, clustering algorithm, and summarization routine feeds the AI the cleanest possible input and produces the clearest possible output.
In practice, that means curating the signature library—verifying descriptions, adding references, and adding context the model can use without launching expensive follow-up queries. It means checking that correlation rules group related alerts accurately and that cluster summaries capture the story an analyst needs in one glance. It means building feedback loops, so user corrections flow back into rule tuning and model retention instead of vanishing into closed tickets. Week by week these stewards review trends: Are analysts overturning too many AI decisions? Do certain signatures generate noise? Is a new clustering pass reducing or raising the rework rate? Their work resembles quality engineering in manufacturing—measure, adjust, and measure again—only the product is situational awareness rather than car parts.
The financial stakes make this shift unavoidable. When labor shrinks and compute grows, every extra token burned on a redundant query or every false positive that triggers an unnecessary containment step lands directly on the budget. Process managers guard against that waste. By tightening signatures, refining clusters, and closing the loop on analyst feedback, they keep AI efficiency high, cloud bills predictable, and the SOC’s overall cost-to-value ratio moving in the right direction. In short, the future “threat hunter” hunts inefficiencies in the system itself, ensuring that automated defenses stay sharp, accurate, and economical.
AI Resistance
Despite the chorus of objections—governance headaches, adversarial-data fears, regulatory hand-wringing, talent shortages, and the perennial “black-box” anxiety—these are speed bumps, not barricades. They surface because people rightly worry about their roles, budgets, and liability; yet none of these hurdles can reverse the economic gravity pulling the SOC toward AI autonomy. Just as the smartphone displaced the BlackBerry despite security qualms, AI will displace labor-centric workflows because it slashes cost, amplifies precision, and unlocks round-the-clock resilience. The real question is not whether the tide will rise, but how quickly each organization learns to surf it—re-skilling analysts into QA stewards, process engineers, and impact arbiters while embedding the guard-rails that turn fear into forward momentum.
Conclusion
Artificial intelligence is doing to the Security Operations Center what cloud computing did to data centers: stripping away manual toil and exposing the real work that still demands human judgment. People are still needed, but their skill sets and jobs will shift. Entry-level analysts no longer click through endless alerts; they verify and improve the machine’s decisions. Mid-tier staff stop chasing indicators and start translating security risk into business impact in real time. Senior hunters turn their expertise inward, fine-tuning signatures, clustering logic, and feedback loops to keep precision high and compute costs under control. Yes, governance questions, model-poisoning risks, and cultural resistance will slow the march, but none of them can cancel the clear financial and operational advantages. The organizations that thrive will be those that embrace the transition—investing in new skills, embedding transparent guardrails, and treating process quality as the new frontline of defense—so their leaner, AI-first SOC delivers stronger security at a fraction of yesterday’s cost.