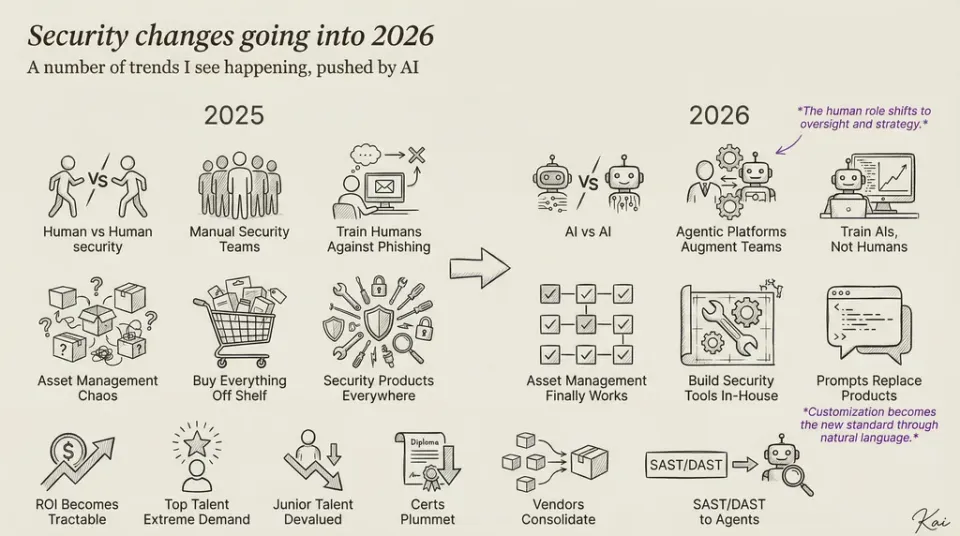
The Evolution of Cybersecurity: From Hacking Culture to AI-Driven Defense

By Chris Jordan
The Early Days: A Culture of Curiosity
For many in my generation, movies like WarGames might have been the spark that ignited an interest in cybersecurity. But for me, it was books like Neuromancer and The Cuckoo’s Egg that truly captured my imagination. I was drawn to the culture—one of constantly solving puzzles, exploring interconnected systems, and discovering the mysteries hidden within the fabric of early computing.
During college, I engaged with what was the internet of the 1980s—primarily through bulletin board services (BBSes). The social aspect was intoxicating. Finding like-minded individuals who shared my passion for computers wasn’t easy, but the ability to connect, chat, and share knowledge across phone lines was revolutionary. Setting up and running a BBS was, in itself, a hack—there were no instruction manuals, just trial, error, and the collective wisdom of the underground computing community.
Breaking and Defending: The Shift in Perspective
As I transitioned into my professional career, I was fascinated by the realization that companies would actually pay me to break into systems and analyze data. But an even more profound shift occurred when I saw that the same organizations that wanted me to break things also wanted me to defend them. Suddenly, I had access to a broader view—watching the tactics of countless hackers and attackers, many of whom operated at levels I had never imagined.
At the time, security was still being defined. There were two prevailing schools of thought:
1. The NSA-driven, theoretical approach based on frameworks like the Rainbow Series, which focused on confidentiality, integrity, and availability.
2. A more practical, hands-on mindset emerging from places like Bell Labs, where security was seen as an engineering problem—one of minimizing vulnerabilities, controlling attack surfaces, and understanding system behavior.
The real challenge came when networking changed everything. Suddenly, we couldn’t rely on physical separation as a security boundary. Authentication, access control, and monitoring had to evolve. And with that shift came a growing reliance on checklists—an approach that I’ve always resisted. Instead of fostering true understanding, checklists turn security into a bureaucratic exercise. The essence of security should be in its models and principles, not just a list of tasks to complete.
Fluency and the Innovation of SIEM
This aversion to checklist-driven security has deeply influenced the way I approach cybersecurity solutions, particularly in Fluency’s SIEM. Traditional SIEMs rely on databases—collect, store, and search. It’s an easy model for programmers because it treats security like a structured problem: write a query, get an answer. But that model is inherently slow and inefficient.
What happens if you remove the database entirely? That’s where dynamic programming comes in. Instead of batch searching historical logs, we analyze data in real time, processing events as they happen. It’s like a bouncer at a club with a clicker—counting people in and out instead of stopping everything to do a headcount. This approach is not only faster but also far more scalable. It allows for near-instantaneous detection of anomalies, something database-driven systems struggle with.
AI in Security: Beyond the Search Box
This philosophy extends directly to how I see AI in cybersecurity. Most companies treat AI as an assistant—something to make human analysts better at searching logs or correlating data. That’s a flawed approach because it assumes AI should work the way humans do. Instead, we should be leveraging AI’s strengths:
- AI doesn’t need enrichment the way a human does; it can hold vast datasets in memory.
- AI excels at pattern recognition, but it struggles with anomaly detection—something humans are naturally better at.
- AI can automate repetitive tasks at scale, allowing human analysts to focus on solving real problems.
One major misunderstanding about AI is that people think it should operate in a vacuum—throw data in, get a result out. But AI needs structure, modularity, and refinement. It should be integrated into security workflows, not just bolted onto existing processes.
The Future of AI in Cybersecurity
As AI evolves, we’ll see it take over more of the first-level analysis in a SOC. The first-tier analyst—often an entry-level role—will increasingly be handled by AI. That doesn’t mean humans become obsolete; it means analysts will shift into validation and higher-order thinking. AI will handle the repetitive tasks, but the real decision-making—determining the “why” behind anomalies—will still require human intuition.
However, this shift presents a challenge: If AI automates entry-level security work, how will new analysts develop their skills? The learning curve can’t be skipped. Just like children need to learn basic math before tackling abstract concepts, cybersecurity professionals need to understand the fundamentals before managing large-scale systems.
The Skills for the Next Generation
This is where the industry needs to change. Too many people enter cybersecurity without a solid understanding of computing fundamentals. When I interview candidates, I often ask them a simple question: How does DNS work? The number of people who struggle to answer that—despite working in security—is alarming.
Future cybersecurity professionals need to focus on:
1. Understanding Computer Science Fundamentals – Networks, authentication mechanisms, operating systems, and memory management.
2. Scalability and Infrastructure – Learning how to manage security in cloud environments, Kubernetes, and distributed systems.
3. Problem-Solving and Pattern Recognition – Developing the ability to recognize anomalies and investigate deeper issues.
4. Continuous Learning and Adaptation – The ability to learn new threats and techniques on the fly, without waiting for formal training materials.
The biggest mistake security professionals can make is relying solely on checklists and predefined processes. The real world doesn’t follow a checklist. It’s messy, unpredictable, and ever-changing. And that’s what makes cybersecurity fascinating.
Conclusion: The Puzzle Never Ends
At its core, cybersecurity remains what drew me to it in the first place—a puzzle. The interconnected world of computers is still full of mysteries waiting to be unraveled. Whether it’s breaking down an attacker’s methods, innovating new defensive strategies, or pushing the limits of AI, the fundamental excitement hasn’t changed.
And for those who are passionate about this field, the challenge isn’t just keeping up. It’s about staying ahead.