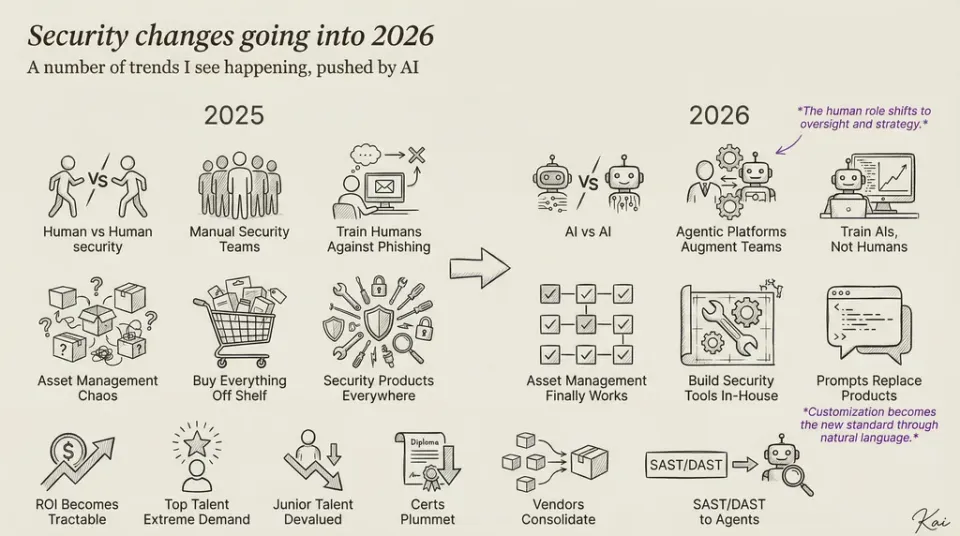
Understanding MCP for use in AI-SIEM/SOAR
if we’re going to move beyond toy examples and build real, automated Gen-AI workflows — especially in high-stakes domains like SOAR or SIEM — we need more than just clever prompting. We need structure. We need security. And we need governance.
A common pattern in AI integrations is to expose APIs that the language model can call based on natural language prompts. These APIs aren’t invented by the AI, they’re defined ahead of time by developers, often using standards like OpenAPI, so the AI understands what functions are available and how to use them. You see this approach frequently in automation platforms like N8N and bot orchestration tools, where workflows are built around these structured interfaces. For example, a developer might define an API that retrieves the weather for a given city and timestamp, and the model is taught to call it when someone asks, “What’s the weather in Paris?” This works well for public or low-risk data, where access control is minimal and API keys are hardcoded or safely shared in runtime environments.
But this approach breaks down entirely when the data being accessed is sensitive. These traditional API mechanisms don’t solve the problem of context-aware, authenticated access. For instance, if a user asks the AI to analyze financial records stored locally or behind enterprise controls, we can’t simply expose those systems through public APIs or bake access tokens into the workflow. This is where Model Context Protocol (MCP) comes in. Instead of using APIs in the traditional sense, MCP provides a governed and authenticated channel for the model to request only the specific context it needs, without exposing the full dataset and without giving the model direct, persistent access to secure systems. It’s a fundamentally different approach: not just defining functions, but enforcing who can access what, when, and why.
Using Calls for Business Applications
So why does this matter? Because if we’re going to move beyond toy examples and build real, automated Gen-AI workflows, especially in high-stakes domains like SOAR or SIEM, we need more than just clever prompting. We need structure. We need security. And we need governance. Model Context Protocol (MCP) isn’t just a way to make an AI “talk to your data”, it’s the critical layer that enforces who gets access to what, when, and under what conditions. It’s how we give AI the context it needs, without giving up control. And in security operations, where access to logs, alerts, identity data, and historical behavior must be governed, this control isn’t optional, it’s mandatory. That’s why Fluency is the first SIEM to natively support MCP, allowing AI developers to query live SIEM data securely and programmatically. If you’re building next-generation, AI-driven security workflows, Fluency is already ahead. In the sections that follow, we’ll unpack exactly how MCP works, why it matters for compliance, and how it forms the foundation for intelligent, safe, and actionable AI in modern cybersecurity.
At its core, Model Context Protocol (MCP) is a service architecture designed to securely provide AI models with access to external data, tools, and memory, without embedding that data into the model itself. Officially, MCP is defined as a protocol for enabling governed, structured, and authenticated access to contextual information during AI execution. The specification breaks MCP into three layers:
- Planner – determines which tools or data sources are needed,
- Retriever – securely accesses those data sources, and
- Dispatcher – formats and delivers results to the model.This architecture allows AI systems to make dynamic, policy-aware requests for context without breaching data governance or exposing sensitive sources.
You can find the formal definition and evolving specification of MCP at its official site: https://modelcontext.org
Video Resources
If you’re curious about the technical architecture behind Model Context Protocol (MCP) — or you’re building AI systems that need to access real-time, sensitive, or structured data — there are some great resources available to help you understand how MCP works under the hood:
- Dan Clarke’s “Getting Started with MCP” offers a recent, straightforward walk-through ideal for learners just beginning to explore the protocol. It clarifies the motivation behind MCP and how it operates in practice. https://www.youtube.com/watch?v=DpyjAKmNwpI
- “MCP Explained in 17 Minutes” dives into why MCP matters, how it solves integration challenges, and walks through the architecture, typical workflow, and real-world use cases in a concise format. https://www.youtube.com/watch?v=G5KyIzV-254
These videos are perfect starting points if you’re new to the concept of MCP and want to see how it functions in real-world settings. They break down the architecture, use cases, and benefits, without overwhelming technical detail.
Beyond Technical Need
Finally, it’s important to recognize that MCP isn’t just a technical convenience, it’s a governance imperative. As enterprises move toward AI-driven workflows, especially in regulated environments, questions of how data is accessed, who can see it, and under what conditions become central to compliance and risk management. This is where ISO/IEC 42001, the international standard for AI management systems, becomes highly relevant. MCP directly supports its principles by enabling stateless, policy-enforced access to data. Rather than storing sensitive context inside the model or granting broad, persistent access, MCP allows AI systems to retrieve just-in-time information through authenticated, auditable pathways. It provides a structured method for enforcing data boundaries, not just technically, but procedurally and contractually. In this way, MCP becomes a cornerstone for building AI systems that are not only powerful, but also secure, compliant, and trustworthy by design.
In the end, MCP isn’t just a helpful tool, it’s a necessary foundation for using AI responsibly and effectively within enterprise environments. As we’ve seen, it enables secure, governed, and stateless access to sensitive data, aligning with both technical best practices and emerging standards like ISO/IEC 42001. But more importantly, MCP is becoming the standard for integrating large language models with real-world data. If you’re working with SIEM data, data lakes, or any security telemetry, and you expect to layer AI on top, you need MCP in place. It’s not optional. Without it, you’re either overexposing your data, underutilizing your AI, or relying on brittle, insecure workarounds. Today, organizations that don’t yet support MCP, or don’t even acknowledge it, are signaling that they haven’t yet caught up to where AI-driven security is going. If you want your AI to work with your most important data safely and intelligently, MCP is how you make that possible.